Vulnerability Assessment vs. Penetration Testing: Key Differences and Why They Matter
TL;DR: In an era of rising breach costs, organizations must harden their defenses. This article explains the key differences between Vulnerability Assessments (broad, automated scans) and Penetration Testing (deep, manual exploitation), and how they work together to reduce risk and meet compliance requirements.
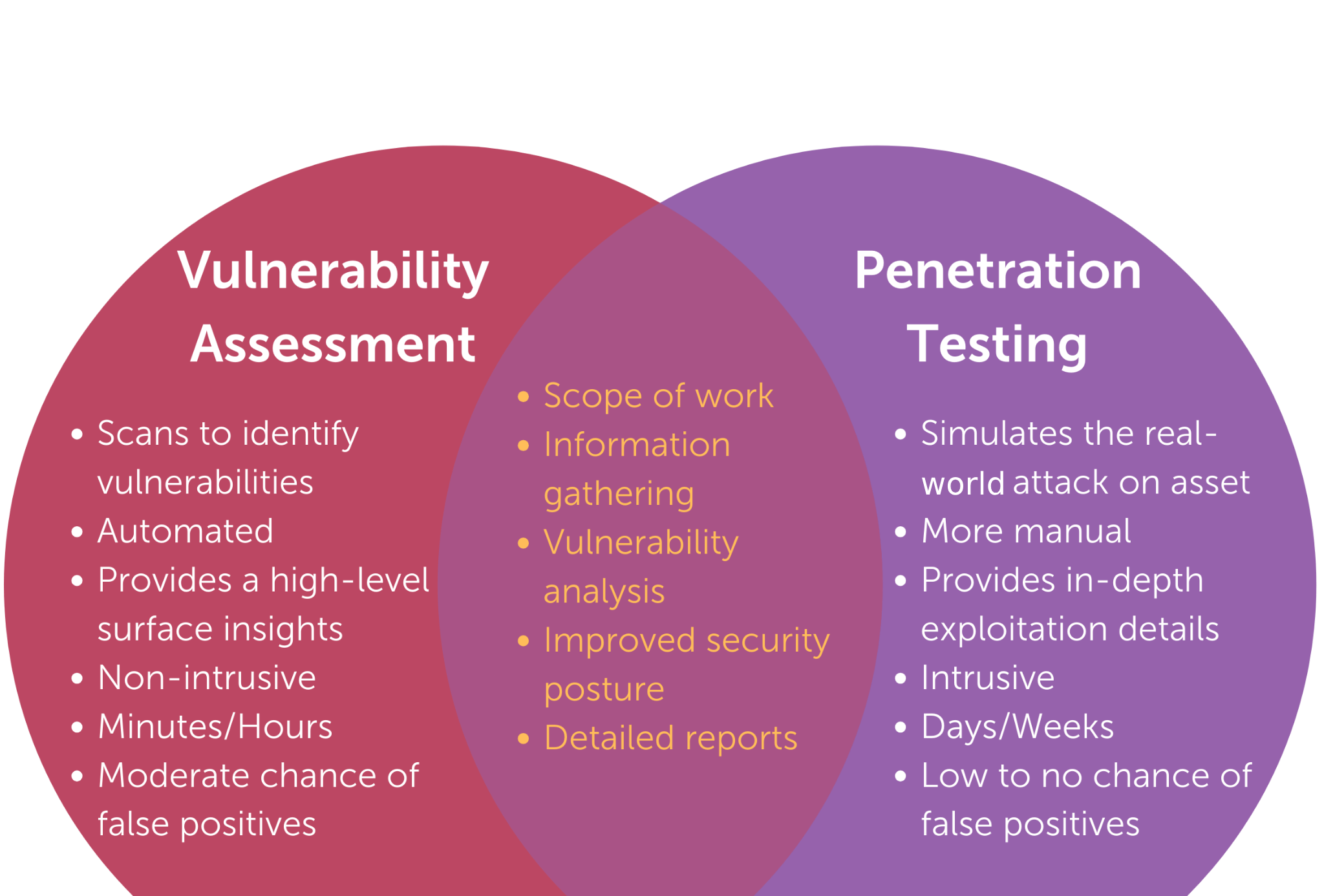
In today's digital landscape, the threat of data breaches looms large over organizations worldwide. According to IBM's 2024 Cost of a Data Breach Report, the global average cost of a data breach has escalated to $4.88 million, marking a 10% increase from the previous year and the highest average on record. This surge underscores the critical need for proactive cyber security measures. Two essential strategies for identifying and mitigating security weaknesses are Vulnerability Assessments and Penetration Testing. While both aim to uncover risks, they differ significantly in scope, methodology, and application.
What is a Vulnerability Assessment?
A Vulnerability Assessment is a systematic approach to identifying, quantifying, and prioritizing security vulnerabilities within an organization's IT infrastructure. Utilizing automated tools, this process scans networks, systems, and applications to detect known vulnerabilities, misconfigurations, and outdated software components.
The primary objective of a vulnerability assessment is to generate a comprehensive list of potential security weaknesses within a system and classify them according to their severity. For example, a scan might identify an outdated or unpatched operating system, a misconfigured firewall, or a known vulnerability referenced by a Common Vulnerabilities and Exposures (CVE) identifier. Once detected, these issues are typically prioritized based on their Common Vulnerability Scoring System (CVSS) score, enabling security teams to address the most critical threats first.
An example of the typical VA workflow includes asset discovery, vulnerability scanning, result analysis, and remediation planning.

Penetration Testing — Explained
Penetration testing, sometimes referred to as ethical hacking, is the practice of simulating real-world cyberattacks on a system, network, or application to identify security vulnerabilities that could be exploited by malicious actors. Unlike vulnerability assessments, penetration tests go beyond identifying vulnerabilities—they attempt to exploit them to determine the real-world impact.
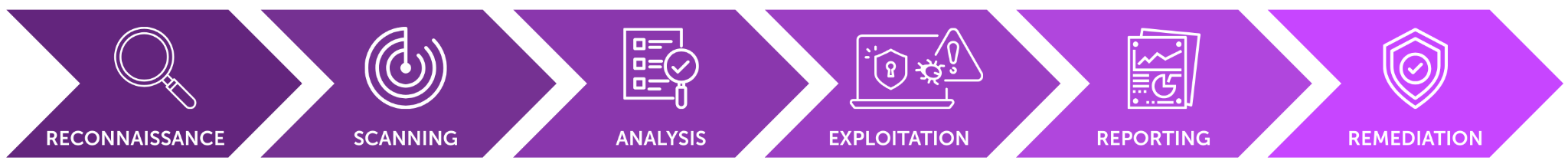
A penetration test involves several phases: reconnaissance, vulnerability identification, exploitation, post-exploitation, and reporting. It is performed within a defined scope and timeline with explicit organizational consent, ensuring safe and controlled execution.
By exploiting vulnerabilities, penetration tests demonstrate how an attacker could breach defenses, move laterally through a network, or potentially gain access to sensitive data. The output is a detailed report outlining exploited vulnerabilities, attack paths, data exposure, and actionable recommendations. While more time-intensive than vulnerability scanning, penetration testing provides deeper insights into the effectiveness of existing security measures.
Vulnerability Assessment and Penetration Testing — Key Differences
Purpose and Scope
Vulnerability assessments aim to answer a key question: “What known vulnerabilities exist in our systems?” They are designed to identify, categorize, and prioritize security weaknesses based on severity, without attempting to exploit them. Vulnerability assessments are ideal for routine security checks, risk management, and compliance requirements, offering a broad overview of an organization's security posture.
In contrast, a penetration test is a targeted and hands-on evaluation that goes beyond identifying vulnerabilities, it attempts to exploit them to determine whether they can lead to actual compromise, such as unauthorized access, data leakage, or system disruption.
To put it into perspective, a vulnerability assessment is comparable to a routine health check-up, such as an X-ray. It is useful for detecting surface-level anomalies across the entire system. In contrast, a penetration test resembles a high-resolution MRI scan. It is intensive, focused, and designed to reveal hidden, deep-rooted issues in the most critical parts of your infrastructure. This makes it a much more thorough examination of your systems.
Depth of Analysis
Vulnerability scanners provide a high-level overview of system weaknesses by referencing known vulnerability databases such as the Common Vulnerabilities and Exposures (CVE) list. They are fast and efficient at detecting common issues like outdated software, missing patches, and security misconfigurations. However, they do not validate or verify whether these vulnerabilities are actually exploitable in a real-world scenario. In other words, they demonstrate plausible exploitability, not proven impact.
Penetration testing, by contrast, is a manual and in-depth process. Skilled testers chain together vulnerabilities, explore multiple attack vectors, and identify complex issues, such as business logic flaws or privilege escalation paths that automated scanners often overlook. They validate exploitability and eliminate false positives by demonstrating real-world impact through controlled exploitation
For example, in a real-world scenario involving a fintech platform, a penetration tester discovered a seemingly low-risk reflected XSS vulnerability in a transaction search interface. While this flaw alone posed minimal direct threat, the tester chained it with an insecure direct object reference (IDOR) in the transaction API and a misconfigured S3 bucket policy. By leveraging these combined weaknesses, the tester was able to escalate privileges and extract sensitive financial records from cloud storage, an attack path that fully bypassed the platform’s centralized logging and alerting tools.
Tools and Techniques
Vulnerability assessments rely primarily on automated scanning tools. These can be configured for non-credentialed (external) scans, which simulate an outsider’s view, or credentialed (internal) scans, which offer deeper visibility into system configurations. Because they are automated, scans are fast, repeatable, and scalable making them well-suited for routine assessments and continuous monitoring.
In modern DevSecOps environments, vulnerability scanning tools are commonly embedded into CI/CD workflows. This allows teams to detect and remediate security flaws early in the development lifecycle, ensuring secure code delivery without delaying release cycles.
Penetration testing, by contrast, is a hybrid approach that blends automation with deep manual investigation. While it often begins with automated reconnaissance, it advances significantly through the use of specialized tools, custom scripts, and expert-level human analysis. Pentesters apply domain knowledge, contextual reasoning, and creative techniques to uncover complex vulnerabilities especially those involving business logic, insecure design patterns, or privilege escalation paths, that automated tools alone cannot detect.
Though AI-assisted tools are emerging, they still fall short of replicating the judgment and adaptability of a human tester, particularly in dynamic or complex environments.
Reporting and Outcomes
Vulnerability assessment reports list all detected issues, categorized by risk level (Critical, High, Medium, Low), and include CVE references along with recommended remediation actions. A well-structured report typically outlines the nature of each vulnerability, its potential impact, and guidance for resolution. However, because these assessments are automated, they often generate false positives or inaccurately assess severity. As a result, organizations may need to manually verify critical findings.
There are two common challenges and pitfalls when processing and interpreting vulnerability scan results:
- False-positive remediation effort: Development teams may spend time addressing issues that aren't truly exploitable, diverting resources from higher-risk problems. Automated tools that perform uncredentialed scans rely on banner grabbing techniques to identify services and their versions, however, these banners can be spoofed or outdated, leading to inaccurate results
- Risk mis-prioritization: Automated tools sometimes flag low-risk findings, such as outdated SSL/TLS ciphers, as high severity, even if the real-world exploitability is negligible. Meanwhile, more serious logic or access control flaws may be underrated.
To mitigate these issues, experienced cyber security professionals should review and validate high-impact findings, adjusting the risk level as necessary to ensure remediation efforts are accurately targeted.
Penetration test reports, on the other hand are fundamentally different. They are narrative and comprehensive, detailing the exact steps taken by testers, the vulnerabilities exploited, and the systems or data accessed. These reports often include screenshots, proof-of-concept code, and a full breakdown of the attack path or "kill chain." Because all findings are verified through active exploitation, the risk of false positives is essentially eliminated.
A typical penetration test report may demonstrate how an attacker could chain multiple weaknesses to escalate privileges, access sensitive financial data, or disable key infrastructure components insights critical for understanding actual business risk.
When to Use Vulnerability Assessments vs. Penetration Testing?
Choosing the right approach depends on your security goals, available resources, and compliance requirements. Vulnerability assessments are ideal for ongoing monitoring and patch management. They can be scheduled regularly, such as weekly, monthly, or at other intervals, depending on the organization's risk appetite. These assessments help provide early detection of common vulnerabilities, enabling timely remediation and reducing the likelihood of exploitation.
Penetration testing is ideal for deep, periodic evaluations, typically scheduled quarterly, annually, or after major environment changes, since even a single line of vulnerable code can expose critical systems to attack.
Hence, it is recommended, Organizations should adopt a risk-based prioritization strategy when selecting assets for penetration testing. Systems handling sensitive data, those exposed to the internet, or those critical to business operations should be prioritized for in-depth testing. This approach ensures limited resources are focused on the areas of greatest potential impact.
Penetration Testing Compliance Standards
Several cybersecurity standards, such as PCI DSS, HIPAA, and ISO 27001, mandate penetration testing at least annually as part of a robust risk management and compliance framework. Here are a few examples:
- PCI DSS: Mandates annual penetration testing (Requirement 11.3).

- HIPAA: Requires regular risk assessments, including VAPT (45 C.F.R. § 164.308(a)(1)(ii)(B)).

- SOC 2, ISO 27001, GDPR: Recommend or enforce periodic VAPT for sensitive systems.
Benefits and Limitations of Each Approach
Both the vulnerability assessment and penetration testing have limitations and tangible benefits of their own:
Vulnerability Assessment
Benefits: Broad coverage, fast and inexpensive
Automated scans can quickly analyze an entire network or application for hundreds of potential issues. They can be run regularly with minimal effort and good costs. Scans produce prioritized lists of vulnerabilities to help teams manage patches in a much better way. Since, they are automated, they can frequently be integrated into continuous monitoring.
Limitations: False positives and lack of context
Vulnerability scanning tools may report issues that are not actually exploitable, so each finding typically requires manual validation. These tools do not actively exploit vulnerabilities, which means they cannot confirm the real-world impact or demonstrate how an attacker might chain multiple weaknesses together. In other words, a scan might flag a potential issue, but it won't reveal the worst-case scenario if that issue were exploited. Some tools provide confidence scores to indicate the likelihood that a finding is valid, however, these scores can be misleading or unreliable and should not be solely relied upon for decision-making.
Penetration Testing
Benefits: Realistic, thorough analysis
Penetration tests provide high-confidence results for identified vulnerabilities because findings are typically verified through exploitation or demonstrable proof of concept. They uncover complex security gaps such as chained exploits or business logic flaws that automated scanners often miss. Penetration test reports include step-by-step evidence of successful attacks and often include retesting to confirm that identified issues have been properly fixed. Additionally, retesting helps verify whether remediated vulnerabilities have been effectively resolved, closing the loop on the testing lifecycle.
Limitations: Time, cost, and scope
Penetration testing is a resource-intensive process that requires skilled security professionals and may take several days to weeks to complete. As a result, it is significantly more costly than automated vulnerability scans and is typically limited in scope to high-value systems or applications. Simulating real-world attacks can carry a small risk of unintended service disruption if not carefully managed. For these reasons, penetration testing is not intended for high-frequency execution, unless the environment is highly dynamic or exposed to elevated risk, such as systems undergoing continuous updates or handling sensitive data.
How Do They Work Together in a Security Strategy?
Vulnerability assessments and penetration tests are complementary components of a well-rounded security strategy. An ideal approach uses vulnerability scanning as the first layer of defense, with penetration testing as a deeper, second layer.
In practice, this combination is often necessary for compliance, as many standards require both continuous scanning and periodic penetration testing. Coordinating these two methods helps organizations benefit from the strengths of each.
Vulnerability scanning offers broad coverage and frequent insights, providing a continuous view of known or potential issues. Penetration testing delivers depth and real-world context, showing what an attacker could actually achieve by exploiting vulnerabilities.
Together, they create a layered security posture routine hygiene through scanning and strategic validation via penetration tests. This dual approach ensures that vulnerabilities are both identified and effectively addressed.
Vulnerability assessments and penetration tests play complementary roles in an effective cybersecurity strategy. Assessments offer broad, automated coverage to detect known issues and maintain ongoing security hygiene. Penetration tests deliver deep, hands-on evaluations by simulating real-world attacks to expose hidden risks and validate controls. Together, they form a layered defense, combining routine scanning with periodic, targeted testing to strengthen your overall security posture, support compliance, and reduce the risk of serious breaches.
SUMMARY
| Aspect | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Scope | Broad coverage of all assets (networks, systems, applications). | Targeted to specific high-value systems or applications. |
| Depth of Analysis | Surface-level detection of known flaws (no exploitation). | In-depth, manual exploitation to validate real-world impact. |
| Tools & Techniques | Automated scanners (credentialed/non-credentialed), CVE databases. | Mix of automated reconnaissance, manual tools, and custom scripts. |
| Frequency | Frequent (e.g. weekly, monthly, CI/CD integration). | Periodic (e.g. quarterly, annually, after major changes). |
| Outcomes | List of potential vulnerabilities ranked by severity (CVSS). | Verified exploit paths, proof-of-concept code, detailed remediation. |
Ready to Strengthen Your Security Posture?
Whether you're securing a new product, preparing for an audit, or just tightening controls, we can help you take the next step with tailored vulnerability assessments and expert penetration testing.
